Block Addictive Content
How to Effectively Block Porn (Updated for 2024)
Implement a porn blocking system for more effective blocking on all devices.

I've been a software developer for over 10 years, seeing first-hand how technology is re-wiring people in harmful ways. Since starting Tech Lockdown in 2020, my primary focus has been helping people block porn.
When dealing with blocking adult content, you'll increase your chances of success by creating a Blocking System - multiple porn blockers and bypass prevention layers that work together - instead of relying on a single porn blocker app.
There are generally two content blocking layers that I recommend for blocking websites:
- Layer 1: Use a DNS Content Policy to block websites and apps in a more comprehensive way.
- Layer 2: Leverage blocking and bypass prevention capabilities that are specific to each type of computer or smartphone.
Blocking Porn with a DNS Content Policy
Layer 1 of my system involves a more comprehensive porn blocker using a DNS Content Policy . With this approach, you can add filter the internet connection on your device to comprehensively restrict access to adult content.
You can connect basically any type of smartphone, computer, or even home router to a DNS content policy.
- Point your Home Router to your DNS Firewall to block adult content on all devices using your home internet connection.
- Install an application or configure the network settings on your computers and smartphones to point to your DNS Content Policy so that websites are blocked even when on 4g/5g or when using a WiFi connection away from your home.
To get started, specify the blocking rules in your DNS Content Policy to filter out pornographic content and even block specific apps.
In addition to creating block rules, you can also enforce Google SafeSearch and even YouTube restricted mode, which helps filter out explicit content within those platforms.
Blocking content with a DNS Content Policy is ideal because it can comprehensively block content based on categories you select so that you don't have to pick each specific website you want to block.
When blocking pornographic content, you might consider a more granular category selection to include "softer" related sub-categories.
Furthermore, if you are trying to block applications , you might need to block more than one domain.
For example, if you want to block tiktok , its not enough to block tiktok.com. The TikTok app would still work. You have to also block a few other domains like tiktokcdn.com to cause the app to stop functioning properly.
A simpler way to do this is to update your DNS Content Policy to specify an app you want to block. For example, selecting the YouTube app would block youtube.com and all associated domains that the app depends on.
If, for some reason, you can't find an associated category or app that fits your website blocking needs, you could just specify a domain that you want to block:
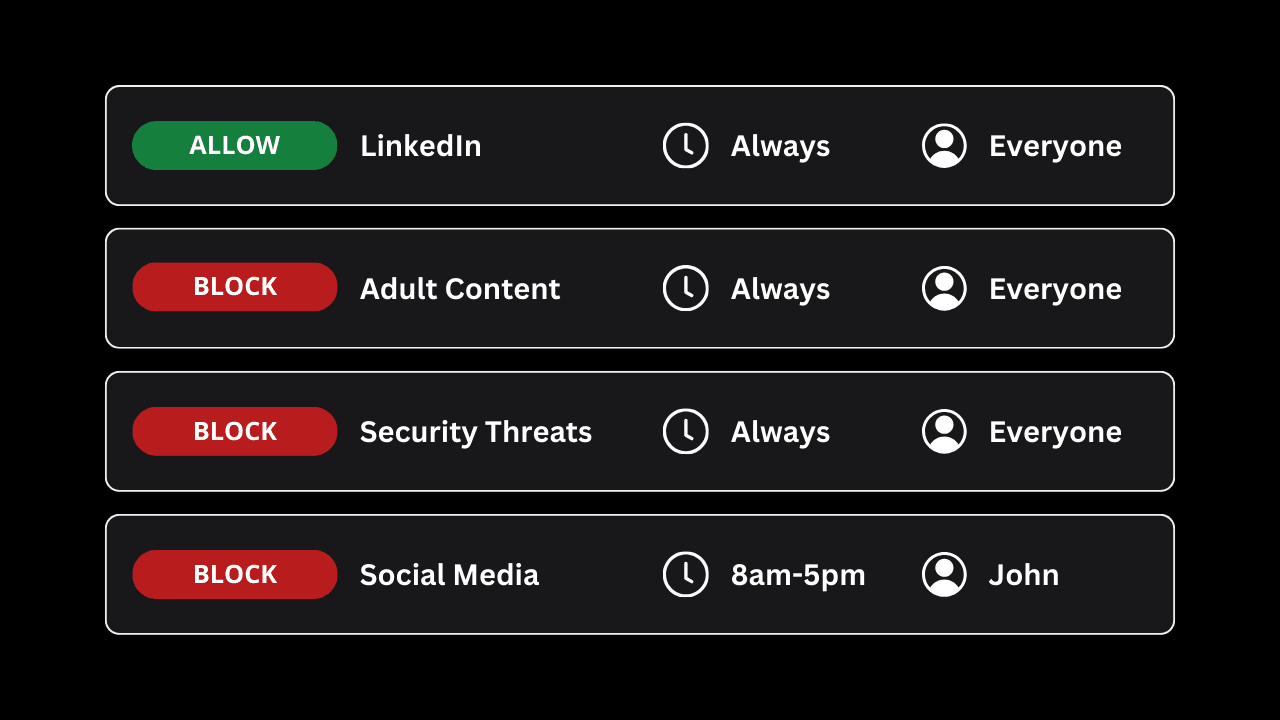
Blocking Apps that Show Explicit Content
One of the benefits of using a Content Policy to block pornographic content is that you can also comprehensively disable apps that you might want to block as well.
It's difficult to quit porn when also using apps like TikTok. This is because certain social media websites can trigger cravings in the brain that lead to seeking out more extreme content. Also, it's quite easy to find explicit content on within these platforms, which leads many people to block them entirely.
If you use a smartphone's parental control feature to block an app , usually this will just prevent that specific app from being opened. However, the app can still be opened via the web browser, which means that you have to block the associated app domains to disable the web browser version as well.
With a DNS Content Policy , blocking an app will effectively disable the app downloaded on the device and the version accessed in the web browser.
We highly recommend that you update your Content Policy to block TikTok .
Another strategy you can use is to block the entire social media category, but selectively whitelist social media apps that are known to be safe.
This is an ideal approach since you can't possibly keep up with every problematic social media app out there, but you know which ones are safe to use (especially when you schedule usage like we'll discuss later).
Scheduling Social Media, Video Streaming, and Internet Usage
Another reason why a DNS Content Policy is a core part of my recommend Blocking System is that you can schedule internet usage: when you access certain apps or websites and even the entire internet.
Here are some scheduling considerations when trying to break adult content addiction:
- Social Media
- Video Streaming apps like YouTube
- The entire internet (at night)
It's simple to do this by first editing your DNS Content Policy to select a category, app, or domain that should be blocked.
Then, assign a schedule to that rule. You can pick days of the week and time ranges to apply the block.
I personally use this approach to limit my access to news and social media to my lunch break.
Otherwise, I always block these categories and apps.
You should also set internet shut off times at night, which is when many people tend to struggle the most with willpower.
This approach is ideal because it takes 4g/5g connections into account, not just your home Wifi.
This doesn't technically turn off your internet, but it lets you block access to everything other than what you specifically whitelist.
For example, I use security cameras at my house that need Wifi to work properly, so I add those services to my allowlist.

Filtering Content on YouTube
In addition to scheduling when YouTube can be accessed, we recommend also filtering content within the YouTube platform. YouTube can cause problems in your blocking setup for a few reasons:
- It triggers impulses that may lead to porn use.
- You didn't seek out certain content - it found you! Now you are dealing with unwanted urges.
The first thing you should do is filter content on YouTube to reduce the chances of stumbling on content or being able to search for it directly.
Get started by adding a YouTube restricted mode rule in your Content Policy:
This will turn on YouTube's filter to block access to certain videos and change what you can search for and what content is suggested to you.
The next thing you should do is block YouTube images so that you don't see clickbait thumbnails:
This can be achieved using the YouTube Images preset you can find when you create a rule:
Blocking YouTube images might seem completely unrelated to blocking porn, but you'll be surprised how much this can help.

Accounting for Private Browsing and VPNs
Private browsing, through the use of VPNs and proxies or other browser privacy features, can create loopholes in a porn blocking system. This is one of the most common bypass techniques you need to account for.
You can add a block rule to your DNS Content Policy with the Anonymizer category selected, which will
block VPNs and Proxies
.
Furthermore, you should implement some of the other blocking techniques that work while using a VPN .
Additionally, many people know about a web browser's private browsing features, which ensure that history isn't saved after the person finishes using the browser.
We recommend disabling private browsing features on smartphones and computers to handle some potential bypass techniques and to also add an additional layer of accountability.
This ensures that when you check the browsers History section that you'll have a more complete picture as to what was being searched for on that device and it will open the door to healthier discussions around internet usage.

Preventing Changes to your Content Policy
If you are self-managing or working with a partner, another scenario you need to account for when blocking websites using a DNS Content Policy:
How do I stop myself from logging in removing a website block by editing my DNS Content Policy?
Some people solve for this by making it difficult to access the account where they manage their Content Policy. However, this is risky and inhibits you from making your Content Policy more restrictive when needed.
My solution for this was to design the Tech Lockdown Content Policy to have a Locked Mode.
When you lock your Tech Lockdown profile , you'll be prevented from removing blocked websites, but you'll be able to add blocked websites easily.
Additionally, the History activity log leaves an immutible trail or breadcrumbs so you can see how your Content Policy was changed.
This added layer of accountability is an important part of a Blocking System where more than one person is involved.
Blocking Porn on Home Wifi Router
Now that a DNS Content Policy is set, it's time to connect your router so that all devices using your home Wifi benefit from content filtering and have more transparent browsing activity.
If you are using Tech Lockdown, you can follow our router installation guide or reach out to our support team to request a guided installation session.
Otherwise, the process looks like this:
- Login to your Router
- Point your router's DNS to the DNS Filter
Router login instructions are found on the back or side sticker of the device that handles your home internet connection.
Then, most DNS Firewalls will allow you to connect by using your router's admin panel to specify IPv4 or IPv6 addresses that correspond with the service.
Once these steps are complete, you should start to see browser activity going forward.
Help with DNS Filter Router Installation

Adding in Additional Porn Blocking Layers
There are additional blocking layers that you can implement on smartphones and computers alongside your DNS Content Policy .
Beginning with computers, there are 3 layers of porn blocking you can use.
- Connect or configure your computer's network settings to connect to your DNS Content Policy
- Hosts File
- Browser Extensions or Screen Time (Mac)
Even if you've configured your home router to point to your Content Policy, you should also install it directly on your computer. This ensures that the computer still filters content, even when on a different Wifi connection or using a hotspot to use the internet.
Additionally, computers have the hosts file, which is a system file that can be used to block websites. Blocking a website with the Hosts File involves adding a line with a domain like this:
0.0.0.0 websiteiwantoblock.com
You can use pre-curated host file lists that let you copy/paste entire categories of websites tagged as Adult Content. Furthermore, you can use browser extensions to block content
An additional benefit to using the hosts file and browser extension blocking layers alongside your DNS Content Policy is that they allow you to block websites while using a VPN .

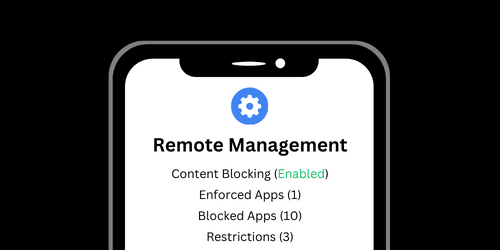
Android and iOS smartphones have a few options that can be used alongside your DNS Content Policy.
- Connect or configure your smartphone's network settings to connect to your Content Policy
- Block content and prevent bypass with built-in Parental Controls or Device Management, and porn blocker apps.
Smartphones can bypass the DNS Content Filtering configured on your Home Router by switching off Wifi and using 4g/5g to browse an unfiltered internet. The way to handle this is to configure the smartphone to always point to your DNS Content Policy and use a few additional blocking techniques.
For example, you can use the iPhone's built-in parental controls to block specific websites or Limit Adult Websites.
However, built-in parental controls on Android and iOS like Apple Screen Time are easily bypassed and lack reliability.
Luckily, Apple provides an alternative to screen time through Device Management that not many people know about and Android devices can be managed in a similar way.
For example, you can use supervised or managed modes to specify app blocklists on Android or iOS:
You can also enforce a Web Content Filter to block specific URLs or limit adult content:
Furthermore, you could use Allow-only mode to block all URLs by default other than the ones you specify.
The device management techniques can be confusing, but we've made step-by-step instructions available to Tech Lockdown members.
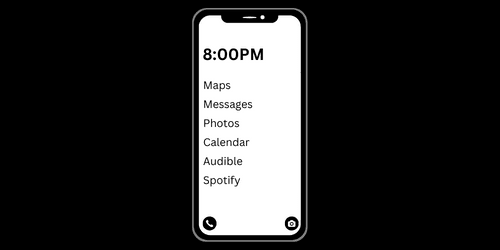
Remove Smartphone Features to Create your Own Dumb Phone
If you are serious about quitting porn and are trying to utilize every possible tool to achieve this, consider transforming your Smartphone into a dumb phone .
This doesn't mean going back to a flip phone, but changes you can make to your current Smartphone to reduce how much dopamine you get from it. Basically, this improves your impulse control and frees up willpower. Ultimately, it helps you re-wire impulsive behaviors caused by smartphones.
A dumb phone lets you configure highly restricted setups with a few options you can choose from:
- Disable the App Store
- Remove Web Browsing
- Make your phone unappealing and plain
Going Further with Bypass Prevention
The main goal at Tech Lockdown is to help people protect themselves from the harmful aspects of the internet. If you are trying to simultaneously block websites and addictive apps while also protecting your devices from security threats, you have an even tougher battle.
Most people aren't motivated to bypass their own virus scanner or privacy tool. But if you are also blocking porn, some people will go through great lengths to get around content blocking. This is a difficult combination of incentives.
This is why I've gone through so much effort to help people prevent bypass of their DNS Content Policy. You want to avoid situations where your DNS protection is unintentionally or intentionally bypassed.
Block Browser Extensions
For example, you can prevent installing unapproved browser plugins and even enforce specific extensions so that they can't be uninstalled or disabled.
Enforce Browser Extensions
Enforce specific browser extensions that you use to block content so that they can't be disabled or removed from the browser.
Prevent changing DNS Settings
For example, on Mac, you can enforce DNS settings.
You can do something similar on iPhone where you install a config file that sets the DNS settings:
Preventing Guest Mode & New User Accounts
Switching to guest mode or creating a new account or profile is sometimes used as a bypass technique on computers or within web browsers, so we show you how to prevent these options.
Prevent Deleting Browsing History & Incognito Mode
Learn how to remove the private browsing features in web browsers, like disabling incognito mode .
Prevent Uninstalling Apps or Browser Extensions
Learn how to enforce apps and browser extensions.
These step-by-step instructions are made available to Tech Lockdown members in your account dashboard in the guides section.
Go Beyond Beyond Basic Blocking
Elevate your content blocking and bypass prevention.
Frequently Asked Questions
Handling VPNs and Proxies
One of the reasons a blocking system is so important is because you have more flexibility over handling conflicts and common circumvention techniques.
Proxies, VPNs, and other DNS providers are common pain-points when it comes to blocking porn. This blocking system takes these circumvention methods into account. Here are the bypass prevention strategies (you should use as many as possible):
1). Block theAnonymizer category using your
DNS Content Policy
.
2). Restrict the ability for users to configure VPNs using supervised/managed device techniques that we mention in the Tech Lockdown guides found in your Tech Lockdown account.
What do I do if I need to use a VPN?
If you need to use a VPN to bypass regional restrictions or connect to work or school, you can block websites while using a VPN using various other methods that don't depend on DNS.
School and Work VPNs
Preventing yourself from logging in and unblocking content
If you are self-managing your own blocking system, it's important that you can't just login and make your Content Policy less restrictive.
The best approach would be to Lock your Tech Lockdown profile .
This ensures that you can still make your Content Policy more restrictive, but can't make it less restrictive.
What is the most Restrictive Setup for Smartphones?
The strictest possible setup for iPhone and Android smartphones involves converting your smartphone into a 'dumb phone' by customizing the device to block access to certain features. Learn how to create your own dumb phone .
Is Blocking Porn Required to Successfully Quit?
In the modern age, I think an effective blocking system is essential for everyone serious about this problem. You are already fighting an uphill battle against the technology you use everyday, which has trillions of dollars of research and development behind keeping you engaged and desensitized.
Here's why:
A habit starts with a cue or a “trigger” that prompts you to follow through on the associated routine.
In response to a cue you “follow through” on the habit by performing a routine (a specific set of actions).
A blocking system will increase your chances of success by reducing how often you are cued and increasing the friction required to follow through on the routine.
Why does it seem so difficult to quit?
The brain's reward system is hijacked by technology to encourage compulsive behaviors. High-speed internet is the force multiplier that turns porn use into a “need” instead of a casual behavior.
The reward chemical called dopamine is intended to further your survival so that you can pass on your genes. Dopamine ultimately drives motivation and the absence of dopamine can result in apathy.
The brain creates powerful, long-lasting associations with behaviors that produce dopamine. This is one of the reasons why cravings for porn can feel so powerful. The association with dopamine is so strong that the brain thinks it's a really important behavior, despite it ultimately being destructive to you.
When it comes to destructive behaviors, such as binge eating, the brain attempts to dampen the pleasure response so that you stop the behavior.
This is known as “desensitization” and it's the reason why you become sick of food that you are overeating or lose interest in the same song after many repeat listens.
You build tolerance and become desensitized to it. The pleasure response is reduced and you ultimately lose interest for a period of time. This is one of the biggest negative effects of watching porn .
Porn addiction probably wouldn't be a widespread problem without high-speed internet. This is because the main way to override desensitization is through novelty - or consuming something new and different.
In the context of sexual behaviors, this is known as the coolidge effect and it basically just means that watching new porn videos can trigger an elevated dopamine response because the brain might not be desensitized to that particular media. This effect helps to explain why porn is so addictive .
Since the brain can create such a powerful association with pornography and dopamine, you will probably find that you need a system for blocking content and preventing bypass as a long-term protective measure – it's not something you will temporarily use.
If you want to learn more about these concepts, read my highlights from the book " Your Brain on Porn " by Gary Wilson.
Is Quitting Even Possible?
Quitting porn is possible, but it depends on why people quit. I mean two things by this:
- Why people give up and make the decision to go back to a behavior that they know to be harmful.
- Why some people make the decision to change (and stick to it).
In the early days of Tech Lockdown, a customer emailed me and wanted help dismantling his blocking system. He was desperate to go back to his old lifestyle and he had ultimately given up.
That's when it dawned on me: people who capitulate tend to feel like they are losing something valuable.
In my experience, it seems like a "catalyst for change" helps some people make the decision to quit and actually stick with it.
For example, a common catalyst for change in a smoker's life might be a negative health event linked to smoking or influence from a loved-one.
For this person, the perceived benefit of the addictive behavior is no longer worth the cost.
In a similar way, there are a few common catalysts for change that you may or may not relate to, but the main reason people are successful at changing is that they are dealing with one of the harmful effects of long term porn use .
How Do I Get More Help?
If you want help setting up my recommended blocking and bypass prevention methods, become a Tech Lockdown member . Membership includes access to step-by-step, premium guides and access to expert support.